ETHICAL HACKING COURSES
How to Hack any Social media, Facebook, Instagram, Twitter, Google, how to bypass 2FA, Advanced Phishing, Advanced Hacking, Advanced Penetration Testing
Penetration Testing, Tutorials, General ·
[Phreaking] : How to Spoof Cell Phone Number
How to Spoof any Phone Number, how to make calls from another phone number, sim swap, Ethical Hacking, Penetration Testing, Phreaking nowadays, Phreaking tutotial
Penetration Testing, Tutorials, General ·
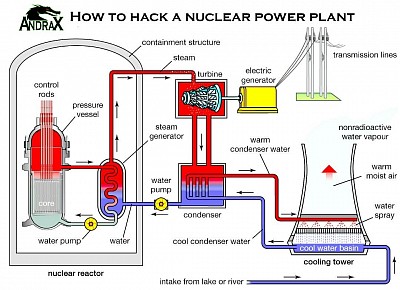
Hacking A Nuclear Power Plant with ANDRAX
How can a nuclear power plant be hacked? How to hack into a nuclear grid, Nuclear power plant Penetration Testing, Advanced Hacking, Advanced Penetration Testing
Bonus – Get a chance to work with Police as Cyber Security Expert* Bonus #2 – Hackers Gold Membership, Access to 200,000+ Tools Bonus #3 – Certificate + License Bonus #4 – 100% Support Guaranteed
Hack from Mobile
Trusted by 90,000+ Students – Join the Community with Top Hackers Organisation Enrolment
Practicals from Android Mobile
Certificate + license
NSDC | Skill India Certified InstituteSubtotal₹9,999.00Shipping
Add to Card
Calculate shipping
Total₹9,999.00
Join Hacking Course with 90,000 other Students
Free shipping
On all orders above Rs 9999
Easy 7 days returns
7 days money back guarantee
International Warranty
Offered in the country of usage
100% Secure Checkout
PayPal / MasterCard / Visa
Trusted by 90,000+ Students – Join the Community with Top Hackers Organisation Registration
Learn and do Practicals Everything from Mobile or laptop
Android Hacking
Wifi Hacking
CCTV Hacking
Live Location Tracking
Traffic Singal Hacking
Kali Linux – Practical Videos
Metasploit
Browser Forensics
Mobile Forensics
Trojons
Spoofing
Social Engineering
200,000+ Tools & 186 Topics
Total 186 Topics with 5 Year Call Support
22 Hacking Courses + 1 Book + Certificate + License90 Days Practical + Hindi Practical VideosTotal 186 Topics with 5 Year Call Support 1,000+ Videos in Hindi / English LanguageRs 34,800 Sponsorship60% Students Learn from Mobile – you can study via Laptop or Mobile – Course is from Beginners to Advance LevelNo Programming Skills required, Anyone can joinHurry! This sale endCOURSE LANGUAGE IS HINDI
Ethical Hacking Online Master Training by Rupesh Gupta
Get trained by India's #1 Ethical Hacker | Start your cyber security career with this in-depth beginner to advanced ethical hacking course.
Lifetime Access
MCEH Certificate
50+ Hours Of Video Lecture
Exclusive Bonuses Worth Rs 5000 For Free
This offer is limited time offer, exclusive bonuses if you enroll today for this master training of ethical hacking.
Bonus 01
01 Premium Hacking Tools Worth Rs 4000 Value absolutely for free
Bonus 02
India's first, best & most selling Blackhat Cracking Course absolutely for free to all who enroll to this course.
Bonus 03
Access to private VIP Hacking community on Telegram where you can ask your doubts & questions to get it solved. You will get free unlimited Access.
Bonus 04
Live QnA calls doubt sessions exclusively by Rupesh Gupta.
Bonus 05
Amazing discounts on all future courses and paid workshops for the students who enroll to this course.
Bonus 06
MCEH Certificate on completion of this training to all the students. MCEH stands for Metaxone Certified Ethical Hacker which is issued by Rupesh Gupta on behalf of his own cyber security
All Ethical Hacking courses
- Whether you want to get your first job in IT security, become a white hat hacker, or prepare to check the security of your own home network, Udemy offers practical and accessible ethical hacking courses to help keep your networks safe from cybercriminals.
All Kali Linux courses
- Ethical hacking is a popular expertise thanks to the stylization of white hat hackers as heroes in pop television and movies. In real life, ethical hacking is just as valiant, and Kali Linux is a powerful tool for getting the job done. Udemy features top-rated Kali Linux classes to help you don your white hat.
All Cyber Security courses
- Whether you want to keep yourself safe while browsing the internet, or brush up on your penetration testing and network security analysis skills, Udemy offers a broad range of cyber security courses taught by top-rated and approachable instructors.
All CISSP - Certified Information Systems Security Professional courses
- Udemy hosts top-rated cyber security experts who are ready to walk you through every step of preparing for the CISSP exam. Whether you're a beginner or advanced security professional, Udemy has a course to help you prepare.
5,548 results for “ethical hacking”Explore Ethical Hacking ,coursesStudents also learnPenetration , TestingCyber SecuritySecurity Hacking, Kali LinuxNetwork, SecurityInformation, Security etc
About the Course
- In this MOOC, you will learn how to hack web apps with command injection vulnerabilities in a web site of your AWS Linux instance. You will learn how to search valuable information on a typical Linux systems with LAMP services, and deposit and hide Trojans for future exploitation. You will learn how to patch these web apps with input validation using regular expression. You will learn a security design pattern to avoid introducing injection vulnerabilities by input validation and replacing generic system calls with specific function calls. You will learn how to hack web apps with SQL injection vulnerabilities and retrieve user profile information and passwords. You will learn how to patch them with input validation and SQL parameter binding. You will learn the hacking methodology, Nessus tool for scanning vulnerabilities, Kali Linux for penetration testing, and Metasploit Framework for gaining access to vulnerable Windows Systems, deploying keylogger, and perform Remote VNC server injection. You will learn security in memory systems and virtual memory layout, and understand buffer overflow attacks and their defenses. You will learn how to clone a Kali instance with AWS P2 GPU support and perform hashcat password cracking using dictionary attacks and known pattern mask attacks.

![Penetration Testing, Tutorials, General · April 04, 2021 [Phreaking] : How to Spoof Cell Phone Number How to Spoof any Phone Number, how to make calls from another phone number, sim swap, Ethical Hacking, Penetration Testing, Phreaking nowadays, Phreaking tutotial](images/th/sd_617d64de1fcb6.jpg?no_cache=1635614984)
![🔥 Bonus – Get a chance to work with Police as Cyber Security Expert* 🔥 Bonus #2 – Hackers Gold Membership, Access to 200,000+ Tools 🔥 Bonus #3 – Certificate + License 🔥 Bonus #4 – 100% Support Guaranteed 🔥 Hack from Mobile Trusted by 90,000+ Students – Join the Community with Top Hackers Organisation Enrolment ✅ 100% Job Assurance, Google Certification with 7 Days Money Back Guarantee 🔥 Practicals from Android Mobile ✅ Certificate + license 🔥 NSDC | Skill India Certified Institute Subtotal ₹9,999.00 Shipping Calculate shipping Total ₹9,999.00 👍Join Hacking Course with 🔥 90,000 other Students Free shipping On all orders above Rs 9999 Easy 7 days returns 7 days money back guarantee International Warranty Offered in the country of usage 100% Secure Checkout PayPal / MasterCard / Visa Comments Popular posts from this blog Ethical Hacking training October 03, 2021 Image The Real Hackers Posts Penetration Testing , Tutorials , General · April 06, 2021 How to Hack any Social Media How to Hack any Social media, Facebook, Instagram, Twitter, Google, how to bypass 2FA, Advanced Phishing, Advanced Hacking, Advanced Penetration Testing Penetration Testing , Tutorials , General · April 04, 2021 [Phreaking] : How to Spoof Cell Phone Number READ MORE Powered by Blogger Theme images by Michael Elkan My photo ETHICAL HACKING VISIT PROFILE Archive Report Abuse](images/th/sd_617d671410b33.png?no_cache=1635615551)
